We’re happy to announce that CFEngine 3.9.0 non-LTS beta is now ready for testing! The established CFEngine release schedule shows that the 3.9.0 final version is due in June 2016, so it’s time to test and fix any remaining issues. Please note that this is a non-LTS release, which means that it is maintained for 6 months from the release date and not supported for CFEngine Enterprise customers, but packages are available for testing.
Running remote bundles
CFEngine 3.9 introduces a simple way to trigger bundles to run remotely by using cf-runagent –remote-bundles to ask a remote cf-serverd to run a given set of bundles. For example:
cf-runagent --hail web01.example.com,web02.example.com \
--remote-bundles fetch_latest_webapp,restart_tomcat
Security is taken into account by requiring that all these conditions are satisfied:
- the bundle(s) already exist in the remote system’s policy
- the cf-runagent client is allowed to connect with allowallconnects or allowconnects
- the cf-runagent client and bundle(s) are explicitly given access to with resource_type bundle regular expressions
- bundle parameters are not allowed; only bundles without parameters can be run
This feature can be very useful if you have one-off tasks that you need to run, like updating or restarting some applications or systems.
Email filtering from CFEngine clients
**

``
body executor control
{
mailfilter_exclude => { ".*Permission denied.*" };
}More inventory out-of-the-box
In 3.9, a mapping from IP address to network interface is provided with the new special variable sys.ip2iface. For Linux platforms with /proc/net/, several new network-related sys variables and functions have been introduced. These include sys.inet, sys.inet6 and sys.interfaces_data, as well as the function network_connections() which returns all current network connections . Process inventory has also been improved with the brand new functions findprocesses() and processexists() which, as their names indicate, return a list of processes and checks for existence of processes based on a regular expression.
Powerful data manipulation
CFEngine 3.9 makes working with function parameters much more convenient
by allowing complex parameters like lists and JSON to be passed directly
without storing them in a temporary variable, e.g. mergedata('[ "thing", { "mykey": "myvalue" } ]'). See the documentation on
Collecting
functions
for more information. When working with data it can often be useful to
do string replacements before using the data in configuration files.
This can now easily be achieved with the new
regex_replace()
function. If you need more advanced data manipulation capabilities, it
is worth looking into the new json_pipe argument to
mapdata().
This should meet all your JSON data manipulation needs by leveraging
external tools such as jq (also see the new def.jq variable).
Hardening of the CFEngine Server
cf-serverd now only accept TLS connections by default, while 3.6, 3.7
and 3.8 cf-serverd accepted both “classic” and TLS connections by
default. If your clients are all on 3.7 or later, there are no
compatibility issues as 3.7 clients (e.g. cf-agent) use TLS by default.
However, if you have clients on 3.6 or earlier you can enable “classic”
protocol on the server side by adjusting
allowlegacyconnects
accordingly. Support for plain http for the Mission Portal and API has
now been disabled by default, so only https-connections are accepted.
This is implemented by redirecting plain http requests to https. If you
need plain http, this can be enabled again by defining the class
cfe_enterprise_enable_plain_http,
e.g. in def.json. The default RSA key-size for Apache has been
increased from 2048 to 4096 bits. However note that the default
self-signed certificate can easily be
replaced.
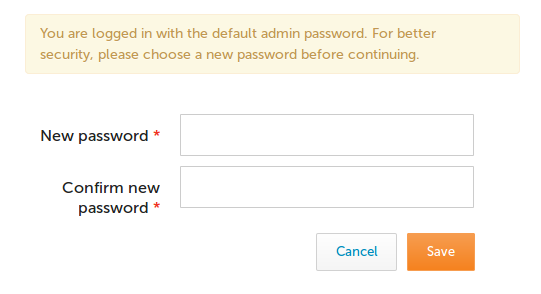
** To further strengthen security, the admin user is now required to
change password upon first login to the Mission Portal in order to avoid
default passwords, as shown below.
 Finally, the files comprising the Mission Portal web application have
received more restrictive file permissions to reduce the risk of attacks
against the web server.
Finally, the files comprising the Mission Portal web application have
received more restrictive file permissions to reduce the risk of attacks
against the web server.
Other improvements
 Several
new CFEngine package
modules
for FreeBSD and AIX have been contributed by the CFEngine community and
released in 3.9; namely freebsd_ports, pkg and pkgsrc for FreeBSD
and nimclient for AIX. This enables FreeBSD and AIX users to leverage
the improved packages: promise introduced
in 3.7
which is more reliable. Internally, the process parsing implementation
in CFEngine has been rewritten to make it more reliable. There have been
several issues with getting the process table and parsing it reliably on
platforms like Solaris where the available ps utilities sometimes mangle
their output columns. This means that promises and functions that rely
on process information will work more reliably on all platforms, but
please note that process: promises no longer match against the entire
ps output, just the command and arguments. This is normally what is
interesting to match against, so most likely your policy will be
compatible, but it is best to do a quick check to make sure. More
information is available in the 3.9 processes:
documentation.
Another high-demand fix aimed for CFEngine 3.9 relates to speeding up
variable expansion over large data
structures. We have worked
really hard to address this complex issue, but unfortunately it did not
make it in time for the 3.9 beta release. However, the fix will be found
in master within weeks and packages including it will be available as
part of the CFEngine Community nightly
builds then. If this fix
receives sufficient community testing once in master, we will consider
releasing it into a stable release, otherwise it will be available in
CFEngine 3.10.0 LTS due for December 2016 at the latest. In 3.9 variable
definitions are included in debug mode, in case you need to see where a
particular variable gets defined and which value it takes. This can help
tremendously in diagnosing a large CFEngine policy. All packaged
dependencies have been upgraded to their latest stable version, in order
to receive reliability and security enhancements. Search for “CFEngine
dependencies” in the ChangeLogs below to see exact versions. For a full
list of the improvements in 3.9.0 beta, please see the Community
ChangeLog
and Enterprise
ChangeLog.
Several
new CFEngine package
modules
for FreeBSD and AIX have been contributed by the CFEngine community and
released in 3.9; namely freebsd_ports, pkg and pkgsrc for FreeBSD
and nimclient for AIX. This enables FreeBSD and AIX users to leverage
the improved packages: promise introduced
in 3.7
which is more reliable. Internally, the process parsing implementation
in CFEngine has been rewritten to make it more reliable. There have been
several issues with getting the process table and parsing it reliably on
platforms like Solaris where the available ps utilities sometimes mangle
their output columns. This means that promises and functions that rely
on process information will work more reliably on all platforms, but
please note that process: promises no longer match against the entire
ps output, just the command and arguments. This is normally what is
interesting to match against, so most likely your policy will be
compatible, but it is best to do a quick check to make sure. More
information is available in the 3.9 processes:
documentation.
Another high-demand fix aimed for CFEngine 3.9 relates to speeding up
variable expansion over large data
structures. We have worked
really hard to address this complex issue, but unfortunately it did not
make it in time for the 3.9 beta release. However, the fix will be found
in master within weeks and packages including it will be available as
part of the CFEngine Community nightly
builds then. If this fix
receives sufficient community testing once in master, we will consider
releasing it into a stable release, otherwise it will be available in
CFEngine 3.10.0 LTS due for December 2016 at the latest. In 3.9 variable
definitions are included in debug mode, in case you need to see where a
particular variable gets defined and which value it takes. This can help
tremendously in diagnosing a large CFEngine policy. All packaged
dependencies have been upgraded to their latest stable version, in order
to receive reliability and security enhancements. Search for “CFEngine
dependencies” in the ChangeLogs below to see exact versions. For a full
list of the improvements in 3.9.0 beta, please see the Community
ChangeLog
and Enterprise
ChangeLog.
Provide feedback
The main goal of releasing the beta is to make sure that 3.9.0 works to your expectations in your environment. So if you get the chance to test out some of the features or perhaps the compatibility with your existing policy, please let us know how it went! The best way to provide feedback is to submit issues relating to the beta in the issue tracker. Please make sure to set the “Affects Version/s” field to “3.9.0 beta”. For general questions and discussions, you can also use the CFEngine Google Group or the #cfengine and #cfengine-dev chat rooms on libera.chat.
Get it!
You can download the CFEngine community 3.9.0 beta packages and source code. If you are an Enterprise customer, please note that 3.9 is a non-LTS release and thus not covered under the support contract. If you would like to test 3.9 beta, the Enterprise beta packages can be downloaded here. Please note that this is a beta release, so we do not recommend installing it in a production environment. We hope you enjoy the new features, and we look forward to hearing about your experience!
Known issues
- AIX does not support alphabetic versions, so 3.9.0 Enterprise beta has version “3.9.99X” (where X is beta build number) on AIX. Final AIX release will have version “3.9.0” like all other platforms.


