All software of any significant size has bugs, vulnerabilities, and other weaknesses. This includes the operating system (OS), libraries, command line tools, services and graphical applications. Across your infrastructure, you should have an overview of what operating systems and software you have installed. Additionally, automated ways of upgrading the OS, as well as packages are desirable. Finally, ways of highlighting problematic hosts (with old operating systems and software) and prioritizing them helps your efforts to upgrade and secure your machines.
Let’s take a look at some ways which CFEngine can help in these areas.
The dashboard
From the first time you install CFEngine Enterprise and open up Mission Portal, its Web UI, you get some useful information:
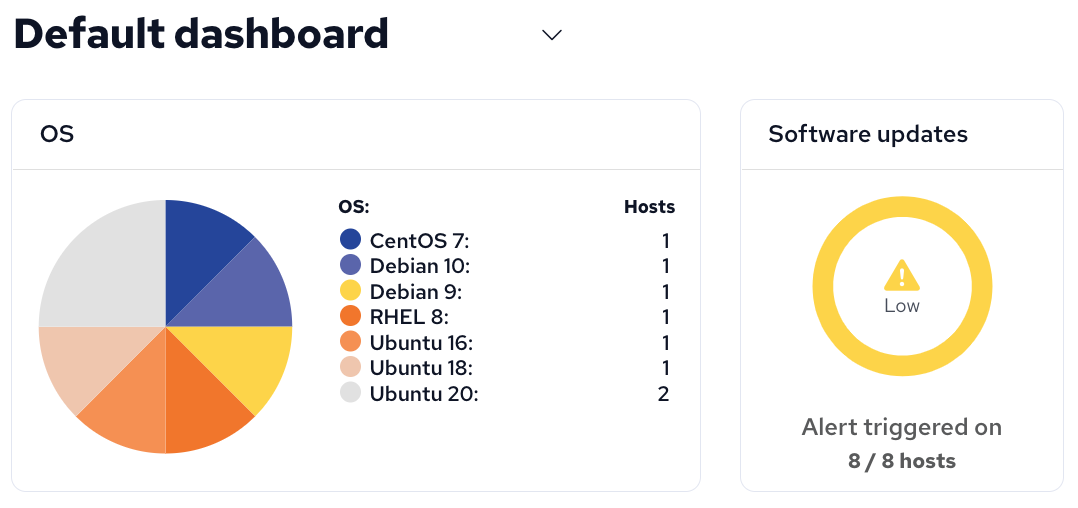
These widgets, available on the default dashboard, shows us our distribution of OSes, and an alert that software updates are available.
Operating systems
Looking at the OS pie chart widget, we can already see some older operating systems. Through some quick googling, I find that Debian 9 and Ubuntu 16 are no longer supported, so we should upgrade them. If you’d like CFEngine to quickly highlight all hosts running unsupported operating systems, there is a module with a compliance report for that:
https://build.cfengine.com/modules/compliance-report-os-is-vendor-supported/
Software updates
The other widget, titled Software updates, indicates that all of our machines have software updates available.
The data here is based on the systems package manager - yum on Red Hat based systems, and apt on Debian based systems.
By clicking on the widget and then the alert inside of it, we get an overview of how the alert works, along with the hosts affected and how many updates are available for each one:
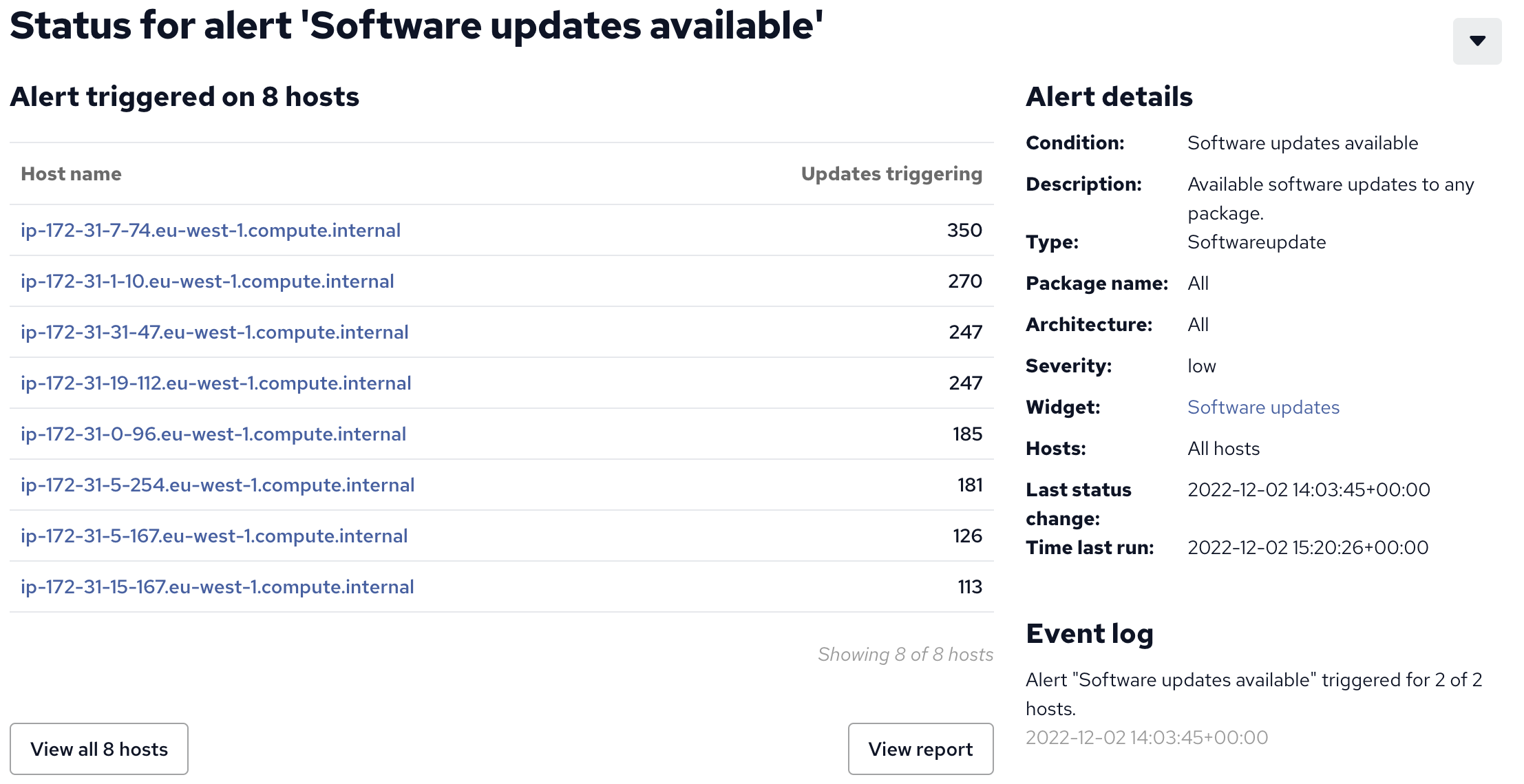
Drilling further down, by clicking on individual hostnames, we can see a report with the exact software and versions available for each machine. Alerts, widgets, and reports are fully customizable, you can take this one step further and highlight only specific packages which you deem important.
At this point, we could start upgrading packages with yum:
$ yum updateOr apt:
$ apt update && apt upgradeHowever, this can be automated with CFEngine. You can do this in policy, or use this module:
https://build.cfengine.com/modules/upgrade-all-packages/
Inventory reports
An inventory report highlights your inventory of hosts (assets), with different reported information about each of them. Use the left navigation bar, click Reports, then Inventory to open one:
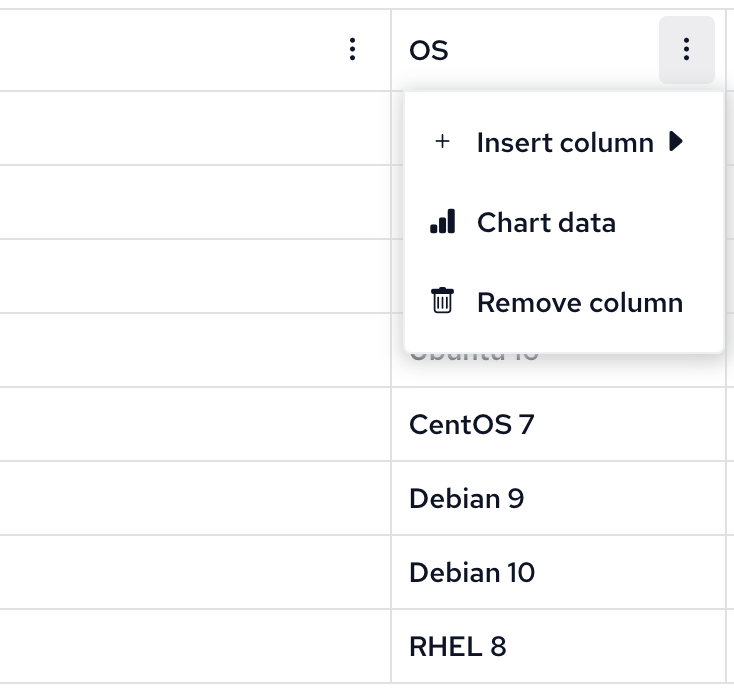
Once inside the inventory report, you can customize what information is shown by clicking the 3 vertical dots, then adding and removing columns:
Uptime
A system’s “uptime” (as indicated by the uptime command) tells you how long the system has been “up”, i.e. how long it’s been since the last reboot.
Since upgrades, especially OS upgrades, typically require a reboot, looking for machines with high uptime can help you identify machines which need attention (upgrades).
In the example below, I removed the column of available memory, and added columns for uptime and Kernel release (versions of the linux kernel in this case), and then clicked on Uptime minutes to sort based on that column:
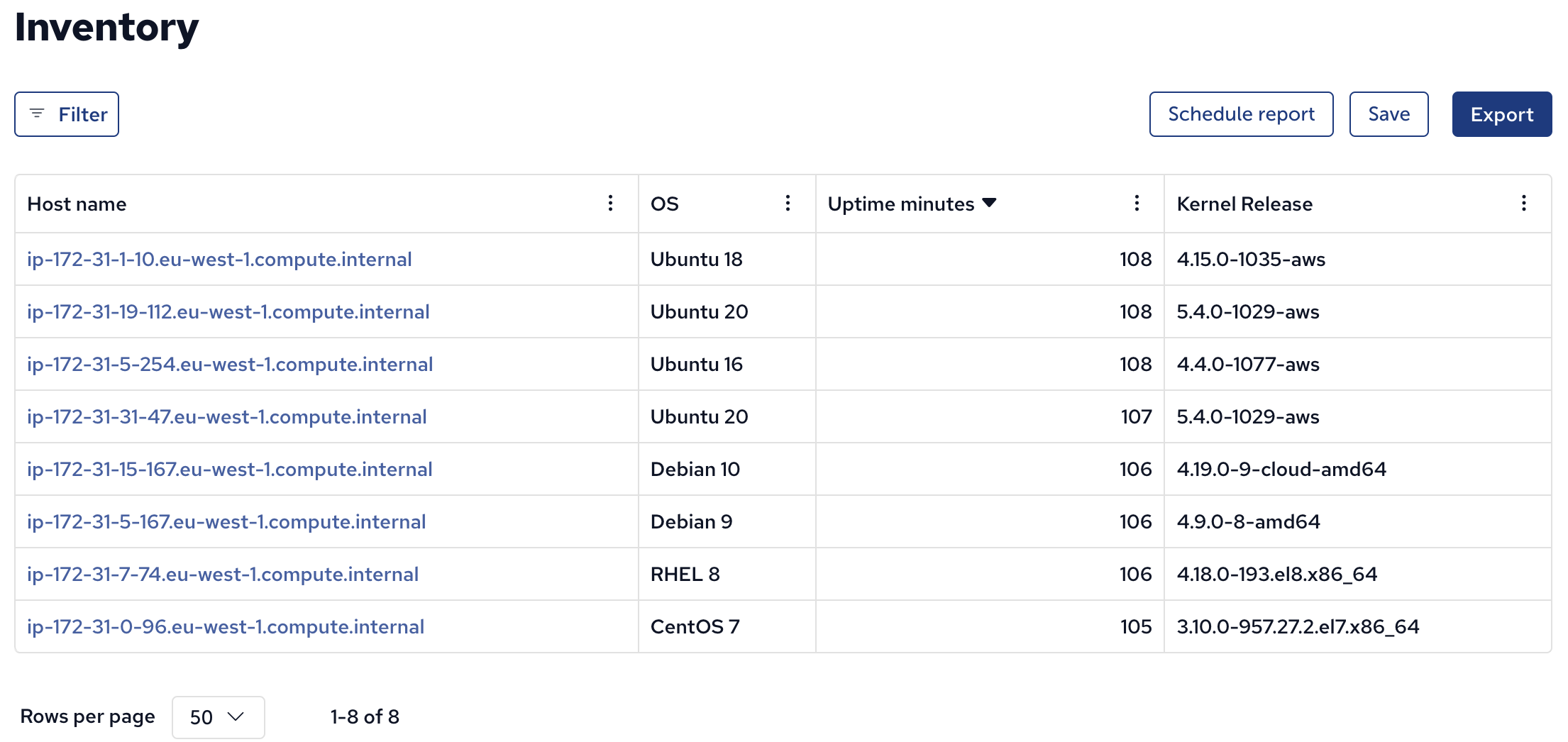
The sorting allows us to see the oldest rebooted machines first. In this case, 108 minutes is pretty good, so no action needed. If you have machines with months or even years of uptime, it might be time for an upgrade and reboot(!).
Security recommendations
Hopefully this guide has given you some ideas on ways to improve the security of your servers and other devices. We recommend that you:
- Ensure you are running recent operating systems and at the very least operating systems supported by the vendor.
- Use automation to help you effectively upgrade software packages.
- Set up reports / alerts to help highlight which hosts need attention and prioritize which hosts to work on first.


