This december, we are posting security advice and modules, every day until December 25th. Now, it’s December 14th, and we’ve gotten to the fourteenth day of the security hardening holiday calendar:
Week 1 summary (1-7/25)
If you didn’t see it yet, we posted a summary last week. Click here to read the security tips for day 1-7.
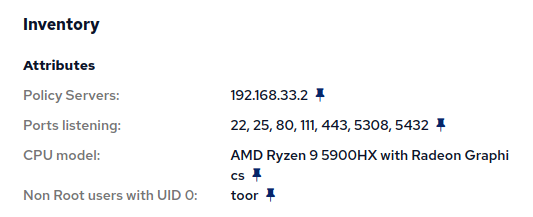
Non-root users with uid 0 (8/25)
On most UNIX-like systems, there is a user called root, with an ID number 0 (uid). Software may assume or expect that to be the case. If the root user is renamed, or another user has 0 as it’s uid, this can cause problems or indicate a misconfiguration. Whenever there are other user accounts with uid 0, you should know about it and investigate it:
build.cfengine.com/modules/inventory-local-users-non-root-has-uid-0
This host adds inventory data to each host:
Recommendation: Look for instances of non-root users with uid 0. Investigate why and fix the misconfiguration (unless there is a good reason why).
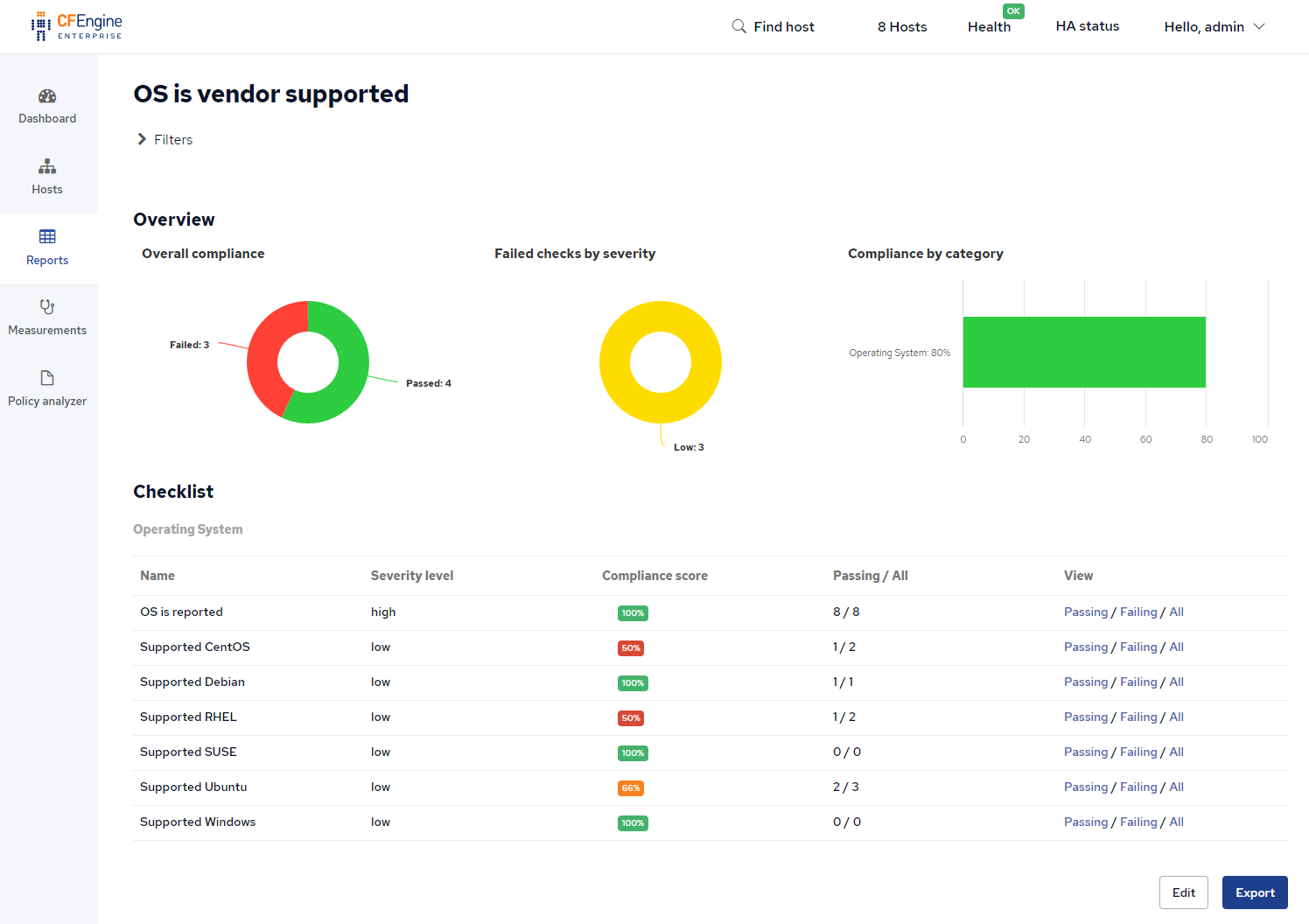
Vendor supported OS (9/25)
When an operating system vendor stops supporting a version of their OS, it no longer receives bugfixes or security patches. Running outdated and vulnerable operating systems can be a big risk. You should have compliance reports which clearly highlight when you are running unsupported operating systems:
build.cfengine.com/modules/compliance-report-os-is-vendor-supported
CFEngine Enterprise 3.18 LTS includes compliance reports, and the report provided by this module easily shows you which hosts are compliant and which ones are not:
Recommendation: Use the reports from this module to see what operating systems are no longer supported. Upgrade the outdated operating systems as soon as possible.
Uninstall openldap-servers package (10/25)
LDAP is a commonly used solution for user authentication and user information storage, but only LDAP servers need the server packages, other hosts only need client packages. You should disable and uninstall the software where it isn’t needed.
build.cfengine.com/modules/openldap-server-not-installed
If you add this module and run cf-agent on a machine with openldap-server installed, it is uninstalled:
[root@hub]# cf-agent -KI
info: Successfully removed package 'openldap-servers'Recommendation: Ensure only the necessary machines have OpenLDAP server installed, uninstall everywhere else.
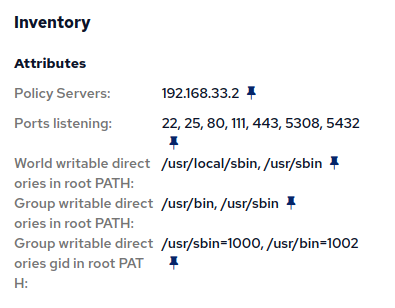
Reports of writable directories in root PATH (11/25)
The PATH variable defines where a shell, or other software will look for programs to run. It’s a list of directories (folders) and differs per user. By writing to the folders mentioned in a user’s PATH variable, you can change the programs ran by that user. If that user has more access than you, this enables a privilege escalation vulnerability. You should monitor all folders in the root’s PATH variable and ensure other users cannot write to them.
build.cfengine.com/modules/inventory-writable-directories-in-root-path
The reporting data provided by the module looks like this:
Recommendation: Monitor the permissions on all folders in root’s PATH variable. Ensure that other users cannot add, modify or delete programs in those folders.
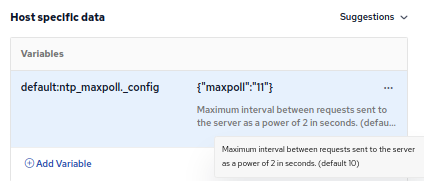
Continuously poll ntp servers (12/25)
Network Time Protocol (NTP) can be used to automatically set the system time. Having accurate time is important for many different pieces of software, and makes the logs and other timestamped data from the host a lot more usable. You should ensure the system time is always correct by regularly polling the NTP server(s).
build.cfengine.com/modules/ntp-maxpoll
In CFEngine Enterprise, you can use the built in CMDB (Host specific data) to configure this per host:
Recommendation: Ensure all your systems have the correct time, by frequently using NTP to poll time servers and set the time.
Allow Only SSH Protocol 2 (13/25)
SSH protocol version 2 (SSH-2) was released in 2006 and includes significant improvements for security, including Diffie-Hellman based key exchange, and integrity checking via message authentication codes. At this point, in 2021, all your SSH servers and clients should support SSH-2, and it is a good idea to enforce only using this newer version of the protocol.
build.cfengine.com/modules/ssh-protocol-2
Recommendation: Use this module to ensure SSH protocol 1 is not allowed on any of your servers.
Sudo should require passwords (14/25)
The sudo program allows other users to temporarily become the root user, to run commands which require additional privileges. Users should be aware and explicitly approve when programs need to use sudo. You should configure sudo to require passwords, to prevent both accidental commands and malicious code from damaging the system.
build.cfengine.com/modules/sudo-requires-passwords
Recommendation: Require users to type their passwords when using sudo, if possible.
Subscribe to the calendar
There are 11 days left of the calendar! To sign up and receive daily security hardening content through Dec. 25th, use this link.