On October 25th 2022 the OpenSSL project team announced 1 the forthcoming release of OpenSSL version 3.0.7. From the announcement we know that a fix will be made available on Tuesday November 1st, 2022 for a CRITICAL security issue.
Note: CVE-2022-3786 and CVE-2022-3602 (X.509 Email Address Buffer Overflows) have been published 2. CVE-2022-3602 originally assessed as CRITICAL was downgraded to HIGH after further review prior to being published.
Affected versions
The vulnerability is reported to affect version 3.0.x and does not impact OpenSSL 1.1.1 or LibreSSL3 4 5. The first stable version of OpenSSL 3.0, was released in September 2021. Older operating systems are likely using OpenSSL 1.1.1, which is not affected.
CFEngine’s use of OpenSSL
CFEngine includes OpenSSL as a part of its packages. No supported releases of CFEngine are using the affected OpenSSL versions. CFEngine 3.20.0 (a non-LTS release) is the only version of CFEngine released built with OpenSSL 3.0.x. It was released July 1st, 2022 with OpenSSL 3.0.46.
Mitigation
We encourage you to read through the official OpenSSL team blog post for detailed information about the vulnerabilities:
https://www.openssl.org/blog/blog/2022/11/01/email-address-overflows/
You will want all hosts and software projects using OpenSSL 3 upgraded to version 3.0.7 (or an appropriately patched version for your distribution, for example 3.0.5-2 in Fedora 36). We recommend you start by identifying all machines with a vulnerable version of OpenSSL installed. Below, we have outlined 2 ways of doing this using CFEngine. Once you have an overview of all affected hosts, start rolling out updates, prioritizing the most critical / exposed parts of your infrastructure first.
Using Custom reports to find OpenSSL version in software inventory
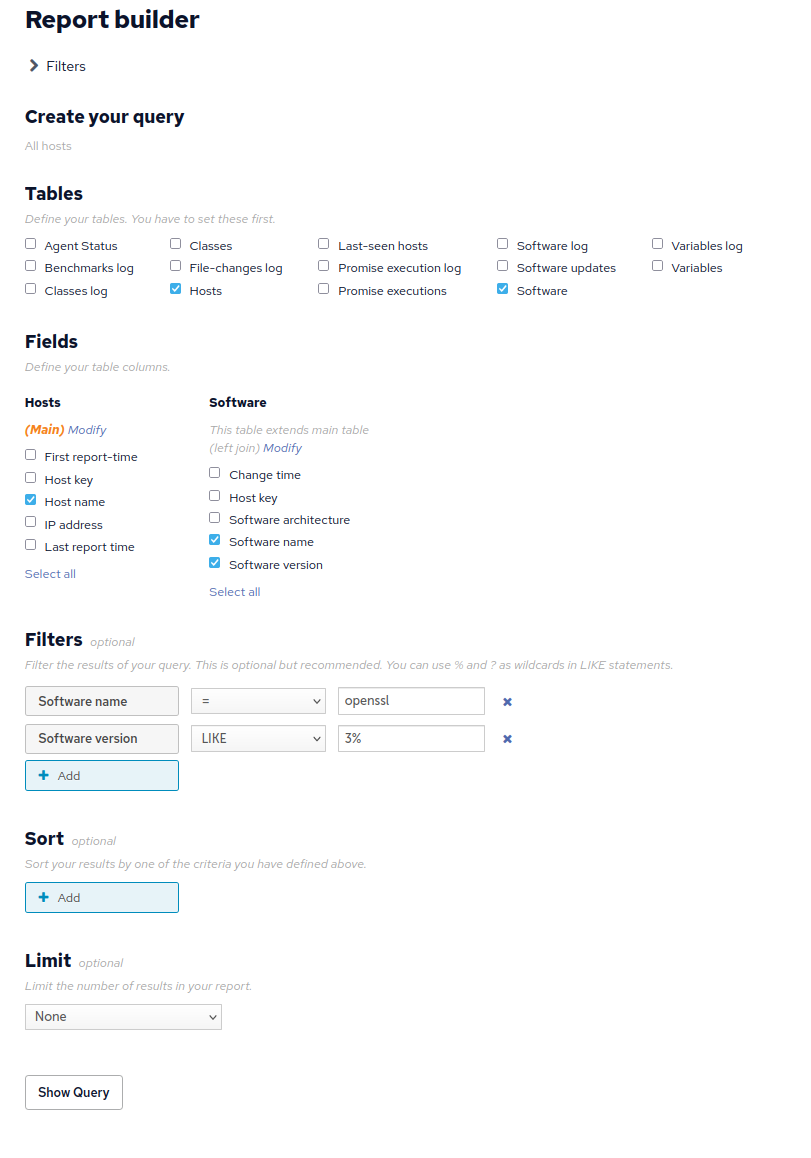
If you are using CFEngine Enterprise you can create a custom report to find hosts with OpenSSL 3 installed.
SELECT
Hosts.HostName AS "Host name",
Software.SoftwareName AS "Software name",
Software.SoftwareVersion AS "Software version"
FROM
Software
LEFT JOIN Hosts ON Hosts.HostKey = Software.HostKey
WHERE
Software.SoftwareName = 'openssl'
AND Software.SoftwareVersion ILIKE '3%'If you don’t know where to enter SQL queries for custom reports:
- Click on “Reports” in the left navigation bar.
- Click on “Custom report”.
- Scroll down and click on “Show query”.
- Paste the query into the text field and click “Run”.
If you get 0 rows, it means OpenSSL 3 was not found anywhere. You can remove the last line of the query to see all versions of OpenSSL.
You don’t need to know SQL to make reports like these, this SQL query was made using the report builder GUI. Instead of pasting in the SQL query, you can fill out the appropriate checkboxes and fields:
A CFEngine Build module to look for installed versions of OpenSSL
We have released a new module to help identify OpenSSL versions installed:
https://build.cfengine.com/modules/inventory-openssl-versions/
This module tries to look for OpenSSL versions in multiple places (it runs openssl, yum, apt, brew) and can detect when multiple versions are installed with different package managers.
It puts the resulting list of versions in an inventory attribute, which can be added to an inventory report:
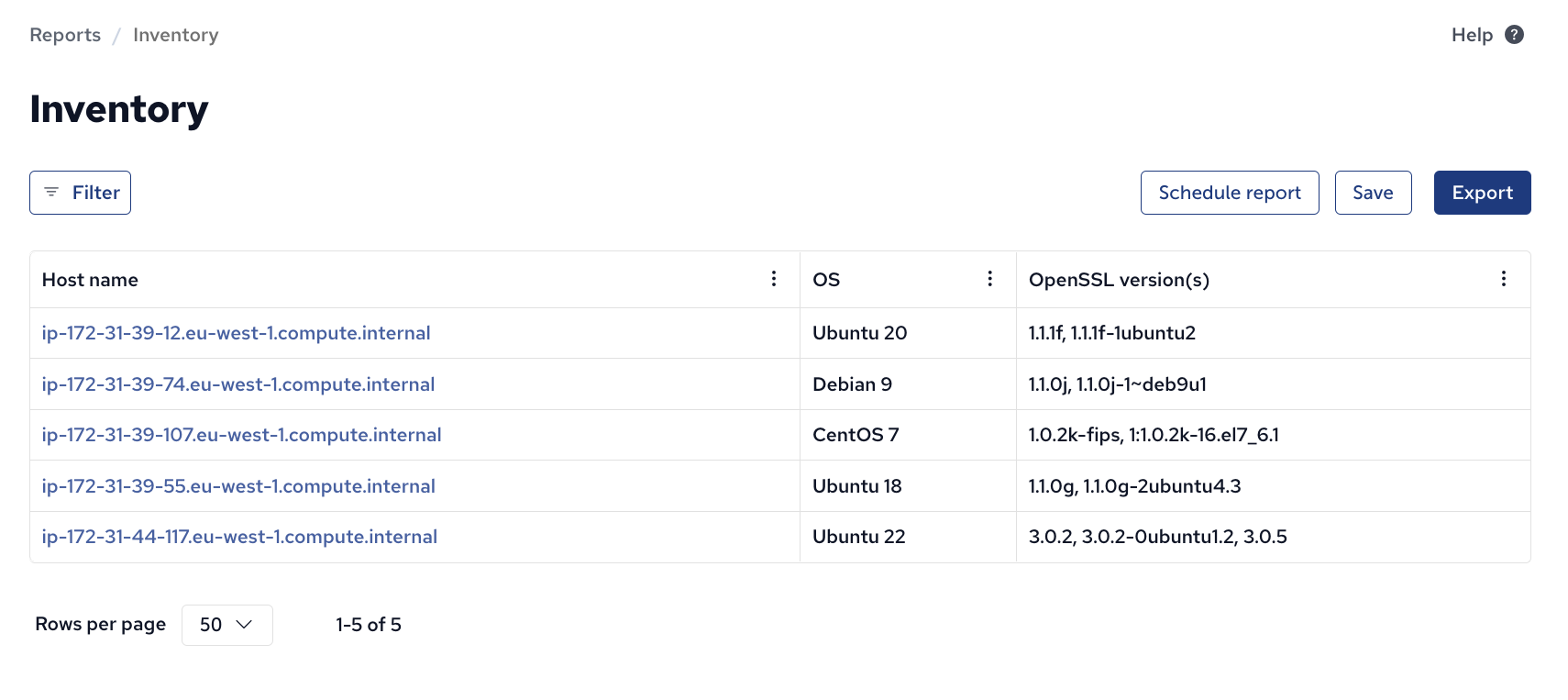
This is somewhat different from what is available in CFEngine out of the box (“software inventory” used above):
- Software inventory relies on one chosen package manager for information about installed versions (
apton Ubuntu,yumon CentOS, and so on). - Installed software names and versions are not normally put in Inventory (Software inventory is separate).
We hope you find one of these methods of identifying potentially vulnerable machines based on OpenSSL versions helpful, and that these vulnerabilities do not have a significant negative impact on your organization and software.
-
The OpenSSL project team announcement of forthcoming release of OpenSSL 3.0.7 https://mta.openssl.org/pipermail/openssl-announce/2022-October/000238.html ↩︎
-
OpenSSL CVE announcement https://www.openssl.org/blog/blog/2022/11/01/email-address-overflows/ ↩︎
-
Sentinel One reports the vulnerability affects 3.0.x and does not impact OpenSSL 1.1.1 or LibreSSL https://www.sentinelone.com/blog/openssl-3-critical-vulnerabililty-what-do-organizations-need-to-do-now/ ↩︎
-
SANS reports the update will only affect OpenSSL 3.0.x, not 1.1.1 https://isc.sans.edu/forums/diary/Upcoming+Critical+OpenSSL+Vulnerability+What+will+be+Affected/29192 ↩︎
-
Synk.io reports the vulnerability will not impact versions of OpenSSL prior to 3.0 https://snyk.io/blog/new-openssl-critical-vulnerability/ ↩︎
-
CFEngine 3.20.0 release announcement https://cfengine.com/blog/2022/cfengine-3-20-released-modularity/ ↩︎