Thank you for following along with our security themed holiday calendar. Today, we summarize the last half of the calendar, in case you missed some days.
Part 1 recap (12/25)
A couple of weeks ago, on the 12th of December, we posted a recap of the first 12 days:
cfengine.com/blog/2022/security-holiday-calendar-part-1
File integrity monitoring with CFEngine (13/25)
On the 13th, we took a look at how you can use File Integrity monitoring in CFEngine for similar functionality to AIDE:
cfengine.com/blog/2022/file-integrity-monitoring-with-cfengine
Recommendation: Set up monitoring for changes in important files, such as /etc/passwd, /etc/crontab, installed software, etc.
This could help you notice an accidental misconfiguration, or a malicious attacker making changes.
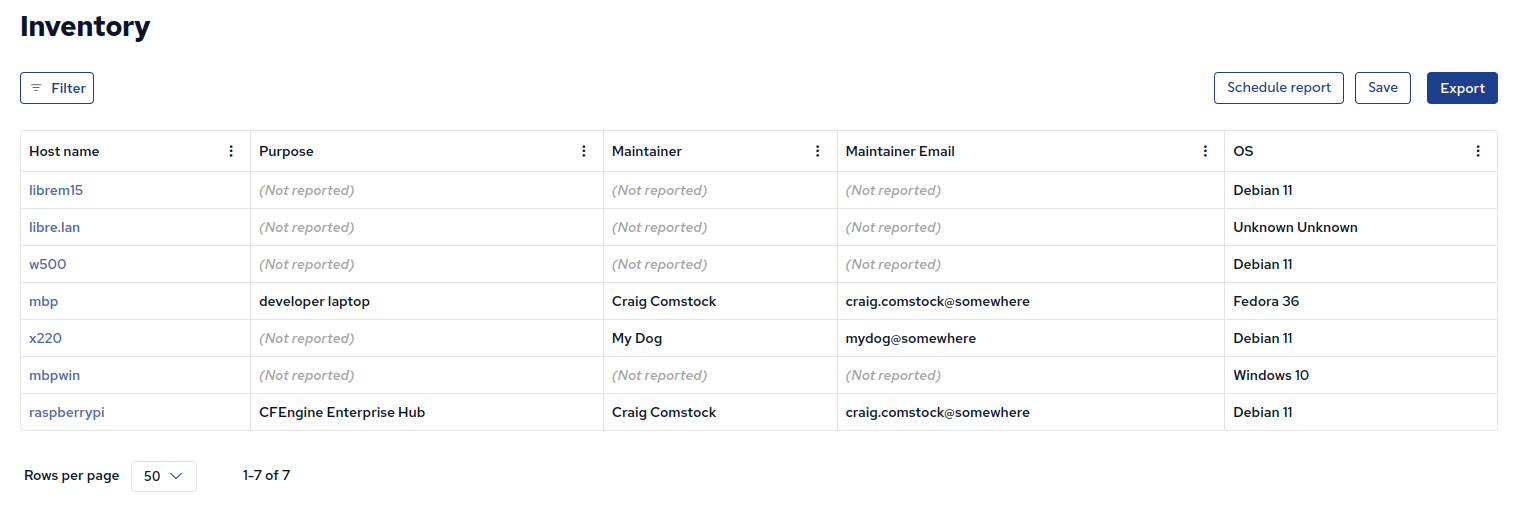
Track maintainers and purpose for hosts in your infrastructure (14/25)
When a host is failing compliance checks, acting suspiciously, or stops reporting, what do you do? Knowing what the machine does and who to contact is crucial:
cfengine.com/blog/2022/track-maintainer-for-hosts
Recommendation: Keep track of who is responsible and what is the purpose for each machine in your infrastructure. As shown in the blog post above, an inventory report showing maintainer’s email address and other relevant information for each host is useful:
Delete .rhosts files in home directories (15/25)
Similar to the .shosts files, the .rhosts files in home directories were historically used for per-user defined host based authentication, in rsh (and ssh).
A global, system-wide, file is preferred, and these files should be deleted if present:
build.cfengine.com/modules/delete-home-dotrhosts
Recommendation: Do not allow user defined host based authentication.
Use this delete-home-dotrhosts module to inventory and delete ~/.rhosts files.
This ensures you are protected in the future, if somebody adds a ~/.rhosts file.
It’s always a DNS problem (16/25)
The bind package provides the named service, for running a DNS server.
Most machines are not DNS servers, and don’t need this package.
To reduce attack surface, this package should be uninstalled when not needed:
build.cfengine.com/modules/uninstall-bind
Recommendation: Ensure only DNS servers use the bind package by uninstalling it on all other hosts (by default).
Explicitly define hosts which are DNS servers and thus need the bind package.
Secure permissions by default (17/25)
Limiting access to system-wide configuration files and folders managed by the root user is very important. In CFEngine 3.21.0 we are changing the default permissions when creating directories to be more strict (secure default):
cfengine.com/blog/2022/change-in-behavior-default-directory-permissions-now-700
Recommendation: When creating directories and permissions using scripts / policy or other software, consider what the permissions should be.
If unclear / unspecified, choose a restrictive default, such as 600 for files and 700 for folders.
Samba! (18/25)
The Samba software enables file and printer sharing, and is typically used in mixed Linux and Windows environments. It can provide an attack vector and has been affected by vulnerabilities in the past. If not used, it should be removed:
build.cfengine.com/modules/uninstall-samba
Recommendation: Uninstall Samba when possible (when it is not needed). For infrastructures or environments which don’t use it at all, uninstall it everywhere. If some of your hosts need to use it, explicitly define where it is needed, and uninstall it everywhere else.
Enforce anything with policy language (19/25)
What do you do when you have a security requirement custom to your organization? When there’s no ready-to-use module? You can write the policy yourself, just like we’ve been writing the modules:
cfengine.com/blog/2022/five-security-policy-examples
Recommendation: Learn CFEngine policy language and enforce any security requirements by writing your own policy / modules.
Uninstall the Apache httpd web server (20/25)
Apache httpd is one of the most widely used web servers on the internet.
If your hosts are not serving websites, and don’t need httpd, it’s best to uninstall it, preventing accidental or malicious activation:
build.cfengine.com/modules/uninstall-apache
Recommendation: Ensure the Apache web server is only running where necessary, by uninstalling it on all other machines (by default). Explicitly specify which machines are allowed to run the web server.
Delete files indicating security issues (21/25)
Many configuration files for cron, at, SSH etc. enable insecure configuration, but are still supported for backwards compatibility. With the delete-files module and the upcoming module input feature, in CFEngine 3.21.0, you can easily delete files across your infrastructure from within Mission Portal:
build.cfengine.com/modules/delete-files
Recommendation: Enforce the removal of files known to be malicious or indicating insecure configuration.
Examples of such files are ~/.shosts files, /etc/cron.deny, etc.
Uninstall unnecessary packages (22/25)
A lot of software is still available to install in package managers, but not recommended to use for security reasons. Old and unmaintained software often has bugs, security vulnerabilities or lack important security features such as strong authentication and encryption. Different compliance frameworks and security hardening guidelines recommend uninstalling various packages, such as:
binddhcp/isc-dhcp-serverdovecot/dovecot-corehttpd/apache2sambasquidtalk/talk-server/talkdtelnet-server/telnetdxinetd
The uninstall-packages module allows you to specify a list of all the packages you want uninstalled:
build.cfengine.com/modules/uninstall-packages
Recommendation: Uninstall packages you don’t need, especially focusing on servers / daemons, and software known to be insecure or have vulnerabilities. Use this module and specify the packages you want uninstalled with module input. Compliance frameworks and security hardening guidelines can help you with ideas beyond the list above.
Upgrade CFEngine (23/25)
Newer versions of CFEngine include features around security and compliance, bug fixes, and other improvements. Take a look at what’s changed and what’s new in the latest release, 3.21.0:
cfengine.com/blog/2022/cfengine-3-21-lts-released-unification
Recommendation: Upgrade to 3.18.3 as soon as possible, and start looking at 3.21, the new LTS series. Stay up to date by always running one of the latest releases on an LTS series.
Enforce strict file permissions (24/25)
It’s important to enforce strict access to system-wide configuration files for software such as SSH, cron, at, etc.
Our file-permissions module allows you to manage permission bits of files, using module input:
build.cfengine.com/modules/file-permissions
Recommendation: Enforce strict permissions on important configuration files such as /etc/ssh/sshd_config, /etc/motd, /etc/crontab, etc.
Happy holidays (25/25)
Today, we’ve wrapped up the holiday calendar for 2022 with this summary. Happy holidays from the CFEngine team:




