In CFEngine Enterprise we collect information from each system in the infrastructure as inventory. Some inventory is available by default, and more can be added using modules or writing policy. You can use inventory information to create a Compliance Report with checks that determine if the information complies with your security requirements. In this blog post, we will use some modules from CFEngine Build which provide inventory data, and build a Compliance Report on top of those.
Add some modules
Assuming you have a hub with a nightly build and have created a Build Project, let’s add some modules which collect inventory:
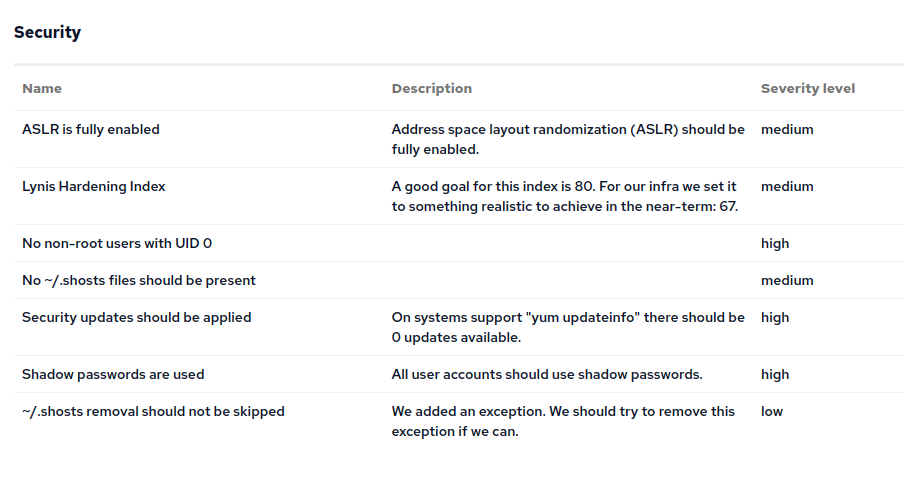
- enable-aslr - Address space layout randomization (ASLR) - collects inventory about the setting on each host.
- delete-home-dotshosts - collects inventory about hosts with
~/.shostsfiles and those hosts which have been given an exception to automated deletion of such files. - inventory-unshadowed-users - collects inventory about users in
/etc/passwdwhich aren’t using/etc/shadow. - lynis - uses CISofy’s lynis system audits - we will add a check for their Hardening Index - an overall number to guage the health of a system
- inventory-local-users-non-root-has-uid-0 - which users have a uid of 0?
- inventory-yum-update-info - information about security updates from
yum updateinfo
We deploy this policy to our infrastructure and wait 5-10 minutes for the information to be available so we can create our new Compliance Report.
Exceptions to the Rule
Many of these modules include providing for exceptions to the policy.
To allow the administrator to skip enforcing policy on specific hosts.
For example, the delete-home-dotshosts module asks for a variable named delete_home_dotshosts:main.exception to be defined for a host to make an exception:
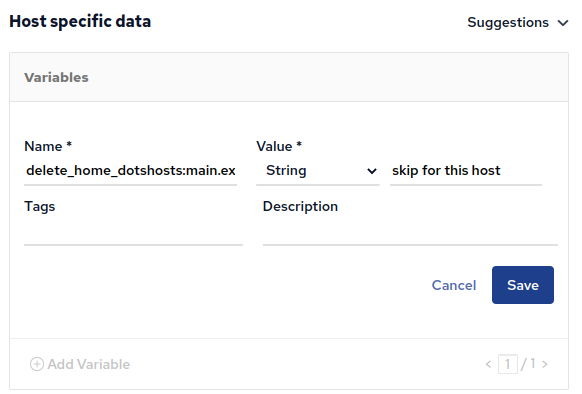
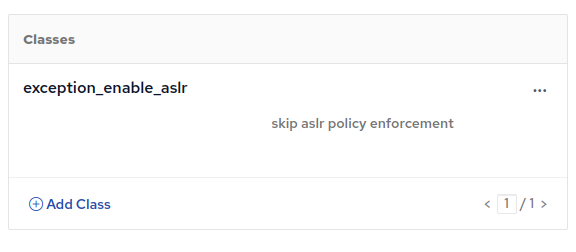
We add an exception for one host for the enable-aslr module as well:
Break things
Now in order for us to see some problems we need to break some things. I used cf-remote to provision some instances in the cloud and now will use it again to break things:
break-things.sh
#!/usr/bin/bash
set -e
clients=ubuntu-22-04-arm64,debian-11-arm64,rhel-8-x64,centos-7-x64
cf-remote sudo -H $clients "sysctl -w kernel.randomize_va_space=0"
cf-remote run -H $clients "touch .shosts"
cat << EOF > bad
emptyfield::9991:9991:testa:/home/emptyfield:/sbin/nologin
starfield:*:9992:9992:testb:/home/starfield:/sbin/nologin
EOF
cf-remote scp -H $clients bad
cf-remote sudo -H $clients "cat bad >> /etc/passwd"
cat << EOF > bad2
toor:x:0:0:toor:/home/toor:/sbin/nologin
EOF
cf-remote scp -H $clients bad2
cf-remote sudo -H $clients "cat bad2 >> /etc/passwd"Inventory report
At this point I run an inventory report and add some appropriate columns to get an overview of the results:
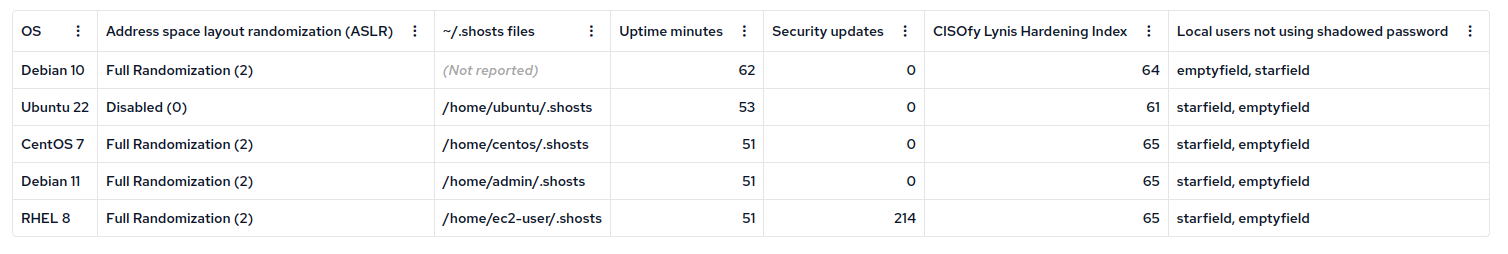
We see that the Ubuntu 22 host has Disabled (0) for an ASLR value.
This is because we added the exception to not enforce our policy on that host.
Create a Compliance Report
From the Reports app in Mission Portal, select the Compliance section and Create a report.
The report is created and you can start editing it (adding checks):

Add a check for the enable-aslr module
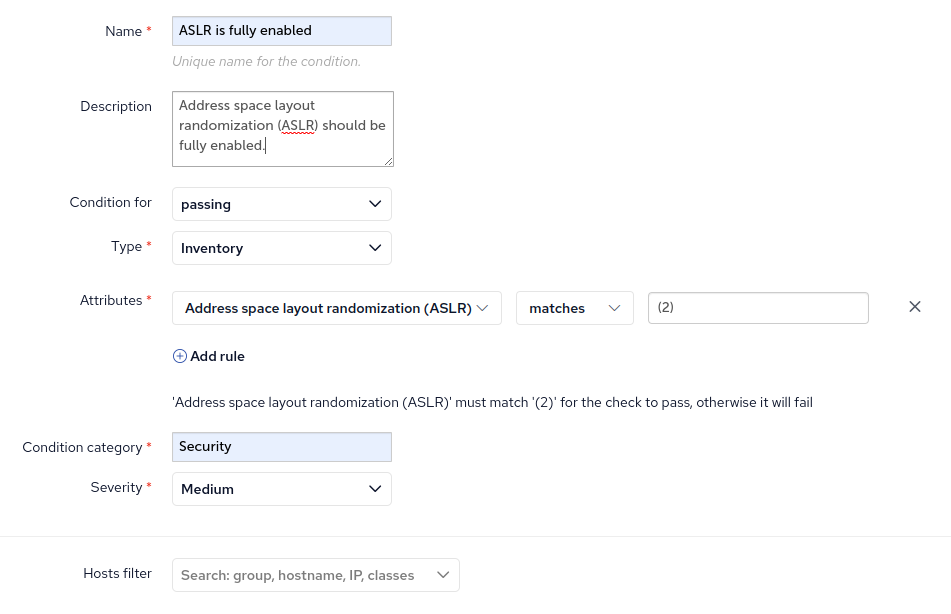
Checks can be based on several different types of information: Policy, Inventory, Software Updates, File Changes or Custom SQL. You can add multiple rules to your check and for each rule can compare the value in various ways such as less-than, greater-than, matches, is or is not reported. Your checks can be grouped together in the report by Category, such as Security, Hardware or whatever custom category you need. Finally, you can filter the hosts involved in this Check by Host tree group, hostname, IP address or CFEngine classes.
The first check I made, checks that Address space layout randomization (ASLR) is enabled, and looks like this:
Add more checks
Similar to the check above, I created a few more for the other modules:
A shiny new Compliance Report!
After saving the checks above, we have a functioning Compliance Report:
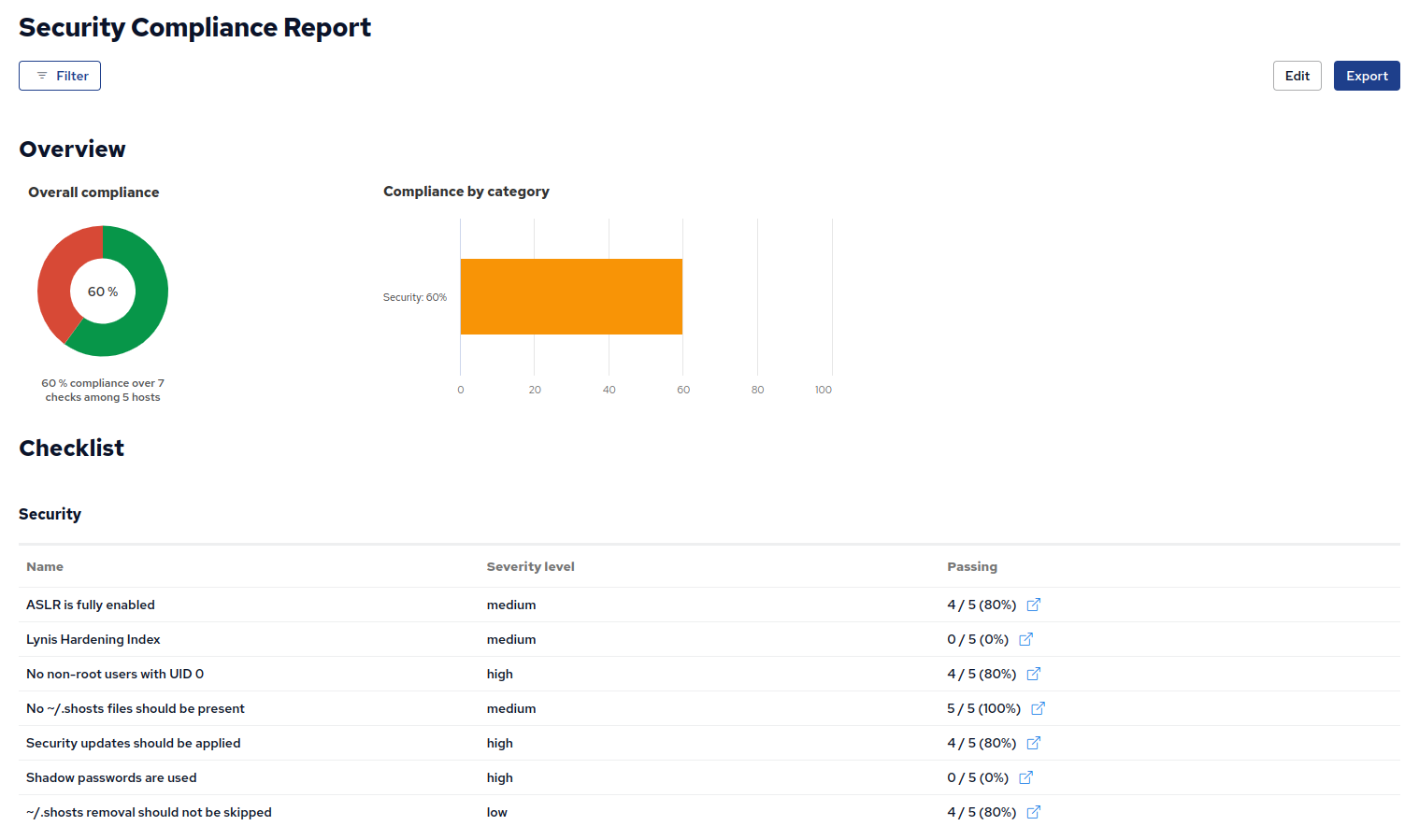
This highlights the state of our infrastructure, showing overall compliance as well as passing / failing host counts and percentages per check. When individual checks are failing, we can click the icon on the right to drill down and find the individual hosts.
Security recommendation: Build custom Compliance Reports to check the reporting data from your hosts, ensuring they are compliant with your security requirements. Inventory data, checks and compliance reports are fully customizable. You can write policy or use modules from CFEngine Build to add additional inventory data. Update and expand these reports over time as your infrastructure grows and security requirements change.


