Security Technical Implementation Guides (STIGs) are an excellent body of knowledge to leverage in securing your infrastructure. With the stig-rhel-7 module you can easily add inventory and remediation policy for RHEL 7 with CFEngine. Do note that as of March 2024 this module does not provide comprehensive coverage but rather an initial 10 findings are implemented.
Setup
To start I installed CFEngine Enterprise on a local virtual machine, logged in and started a new Build project with the stig-rhel-7 module added and configured to enforce (as opposed to only warn).
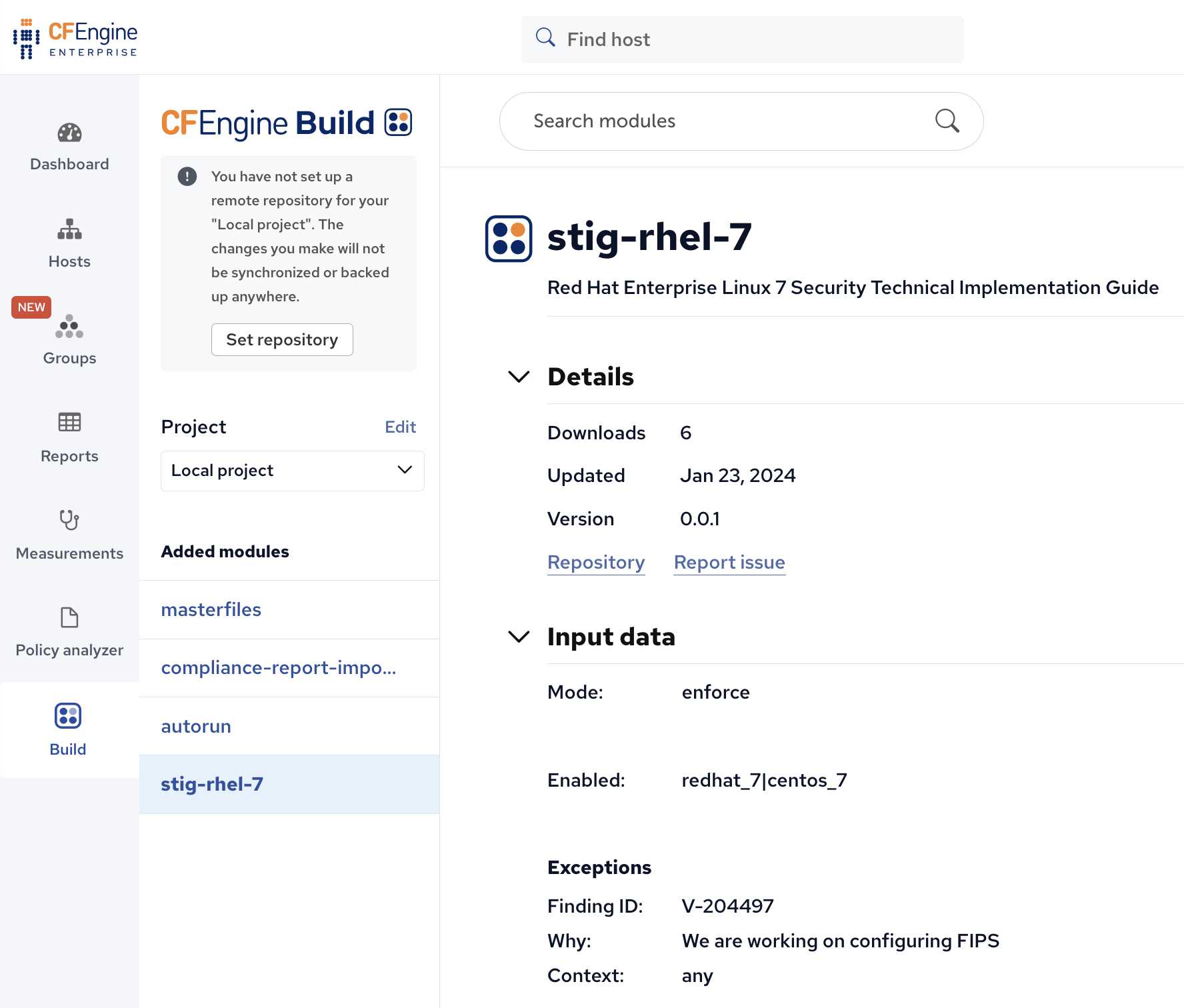
Try it out
The STIG entries which we currently have remediation measures for involve uninstalling software which generally should not be installed for security reasons: rsh-server, ypserv, telnet-server, vsftpd and tftp-server.
After some searching at pkgs.org I found a vsftpd rpm file to install to test compliance and remediation.
curl -O http://mirror.centos.org/centos/7/os/x86_64/Packages/vsftpd-3.0.2-28.el7.x86_64.rpm
sudo rpm -i vsftpd-3.0.2-28.el7.x86_64.rpmAfter installing that package I run the policy and see that the software is removed as requested by the enforce setting.
R: rhel_7_stig:V_204497 is Enforcing without exception but automatic remediation is not available
Warning: RPMDB altered outside of yum.
info: Successfully removed package 'vsftpd'
R: rhel_7_stig:V_204594 is Enforcing without exception but automatic remediation is not available
R: rhel_7_stig:V_204502 is Enforcing without exception but automatic remediation is not available
R: rhel_7_stig:V_204425 is Enforcing without exception but automatic remediation is not available
R: rhel_7_stig:V_204424 is Enforcing without exception but automatic remediation is not available
Compliance reports
Additionally I can view the state of these other findings in my entier infrastructure with our compliance reports.
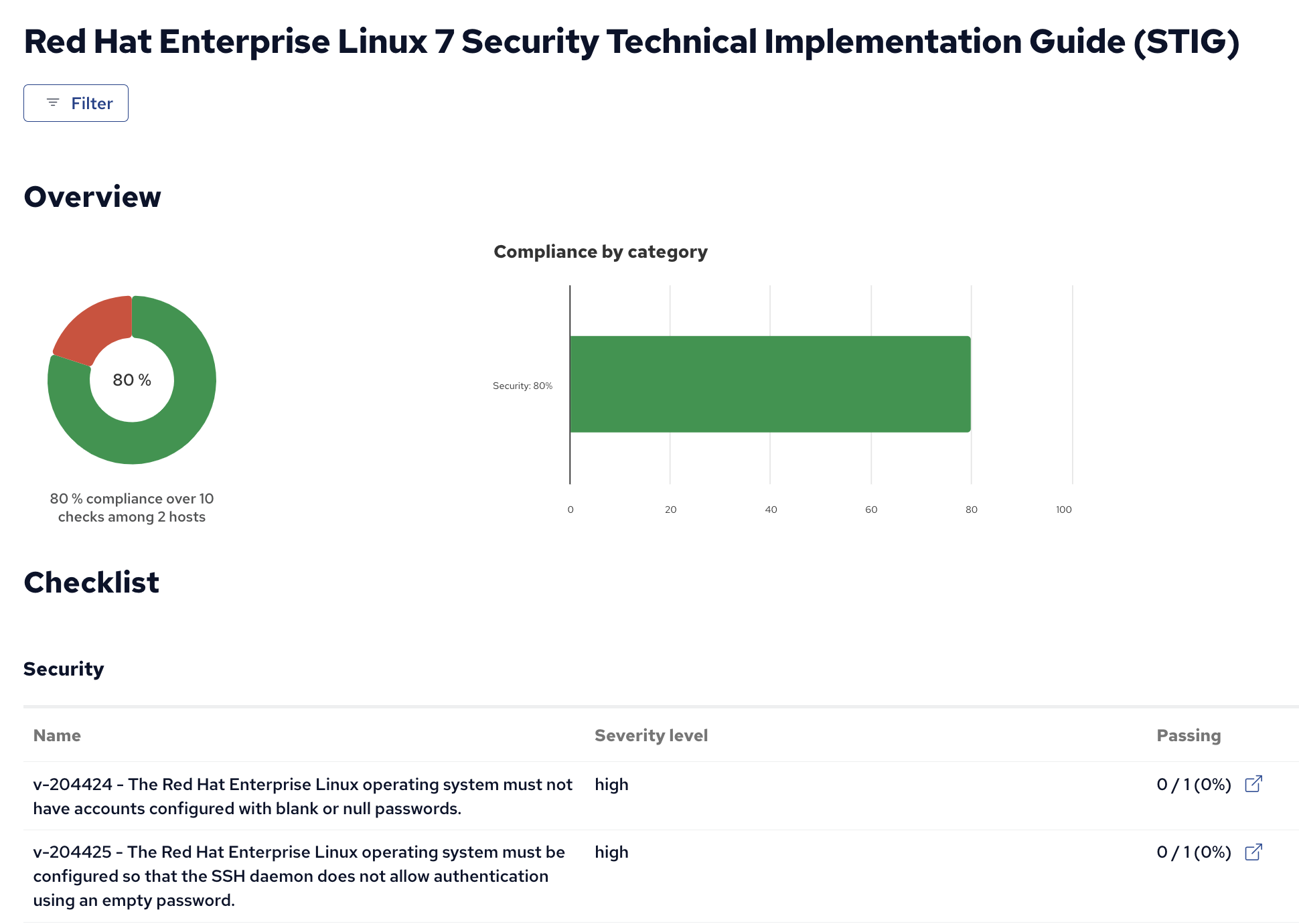
A link is provided to drill down and see which hosts are affected by what findings.
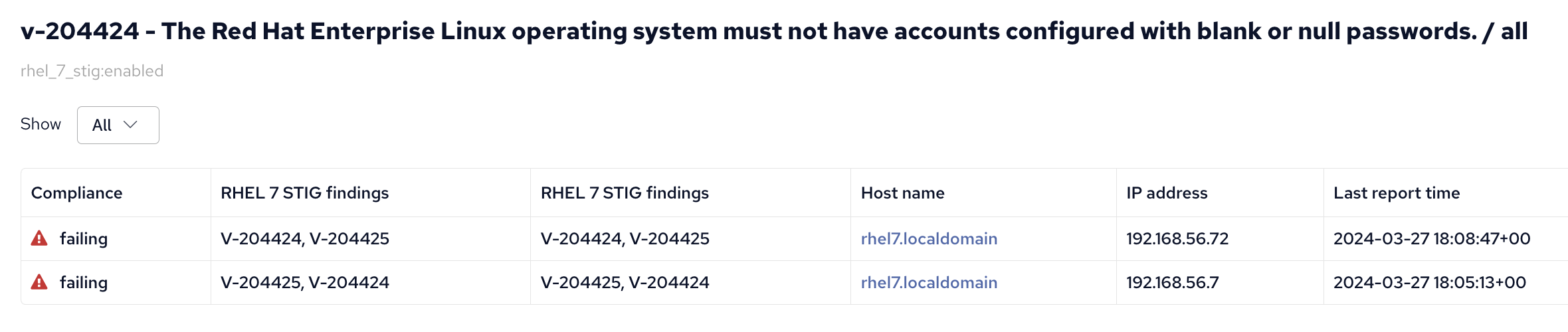
Contribute
Help us make this module more comprehensive. Please consider contributing!
Questions?
If you have questions or need help, reach out on the mailing list or GitHub discussions. If you have a support contract, feel free to open a ticket in our support system.


